Note: The details in this story are gathered from both our perspectives and the Hackers' perspectives. Yes, we had a calm, civil conversation with them afterwards. What can we say, we needed the scoop.
The badassery began with the Hackers (congrats, you're important enough to have your very own pronoun!). The time is Friday morning. Part way through their first period class, the Hackers decided they didn't want to do their online research anymore. So, obviously, they did what any bored Lynbrook student would do. Attempt to hack a friend's email account just to mess with them. Except the Hackers must've really been feeling the Spoons spirit because, they thought to themselves, why not hack the Goderators' (real) email account and mess with 265 people simultaneously!
A real facepalm moment for us. Come on, now. It was too easy for the Hackers. When did we login? Probably the day before, since we need to check things every day. When was the account created? Probably January, since Spoons started in February. And with that, they were in. Props to them for thinking of that route (but again, we do not condone hacking by any means). Once in, they changed everything. Password. Recovery email. Recovery phone. They found out that our more sensitive files weren't in there (tybg), but they decided to send a mass email to gather information from all the Spoons players. And, on the way, they sent some phony emails to Trump Card participants telling them that they had won. After all, why not abuse their newfound power?
When we Goderators got to our second period eyes, bleary-eyed and asleep, we were each confronted with people who ran up to us and shoved the email in our faces. At first, we didn't think much of it. After all, it was probably just another one of those fake email addresses that changed a letter or two trying to screw with people. Which was perfectly valid and kind of funny, to be honest. But when we saw the actual email address it was sent from, we flipped out. Then, Rags checked his own inbox (our original recovery email) and saw a bajillion unread emails titled “Your Account Password Has Been Changed” and “Your Recovery Email Has Been Changed” and “Your Recovery Phone Number Has Been Changed”.
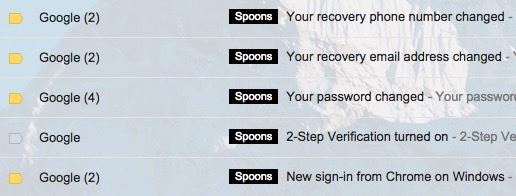 We were not so bleary-eyed and asleep after that. Disregarding everything going on in class (which, let's be honest, is normal for most of us), we texted each other, freaked out, and tried recovering the account through our phones. After failed attempts to login, we saw the faulty security questions. And we saw the changed recovery email and recovery phone number, which Google showed us as “(***) ***-**##” (won't actually be showing you the last two digits). Well, shoot. Someone changed our only way of retrieving the information to get us back into our account.
We were not so bleary-eyed and asleep after that. Disregarding everything going on in class (which, let's be honest, is normal for most of us), we texted each other, freaked out, and tried recovering the account through our phones. After failed attempts to login, we saw the faulty security questions. And we saw the changed recovery email and recovery phone number, which Google showed us as “(***) ***-**##” (won't actually be showing you the last two digits). Well, shoot. Someone changed our only way of retrieving the information to get us back into our account.
Tutorial was a high-speed chase. We took a quick time-stamped photo so that when we did recover the account, we could send an email with proof that we had gained control of it back. We called this Hacker's number. No answer. So we checked all the possible places he/she might be. Iams' room? No. AP Physics? No. Bale? No. Physio? No. A lot of heads turned as we barged into random classrooms, scanned all the faces, and left without a word. Every few minutes, someone would yell “HEARD YOU GOT HACKED”, and we'd yell back “WE TRACED IT”. On the outside, we were badasses. Inside, we felt giddy. This was frickin cool. But, of course, we do not condone hacking.
The Hackers felt badass. The Goderators felt badass. All around badassery.